It does seem to clarify some of the points made by the panelists.
Category Archives: Packet Shaping
More Liveblogging from NANOG Net Neutrality Panel
Question from a provider: VoIP traffic prioritization from essentially our own service?
Moderator: One thing that won’t be allowed is prioritizing your own service over someone else’s similar service; that’s almost the whole point. FCC person: This is contemplated in the document. Existing services wouldn’t have to be reworked rapidly. Seeking input. Reasons to be concerned. Monopoly over last mile has a position to differentially treat such a service. This is one of the core concerns.
Q: Giving the same priority to somebody else’s similar VoIP service is essentially creating a trust relationship; how much traffic will the other service provider send? Continue reading
Exabyte Flood As Politics
 Control or profits?
Which does Wall Street want?
Control or profits?
Which does Wall Street want?
Slashdot finds a post by Ars Technica spelling out how the Nemertes report saying the Internet may get clogged by increasing usage is just part of a political campaign to use increasing Internet traffic as an excuse to nuke net neutrality. A campaign going on since at least January, when the Discovery Institute’s Brett Swanson posted “The Coming Exaflood” in the Wall Street Journal. Beware the thousand thousand petabyes!
My favorite piece of the campaign is this one:
We should not fear the exaflood, however. It is key to the innovative new services and applications that appear almost daily. Consider the growing number of universities that are making course lectures available online, often in real time. Or telemedicine programs that are transmitting medical images and linking patients with distant specialists for real-time consultations.No reason to fear the deluge! The telcos will protect you. As long as they don’t have that nasty net neutrality in the way, Continue reading— Bring On The Exaflood! Broadband Needs a Boost By Bruce Mehlman and Larry Irving Washington Post, Thursday, May 24, 2007; Page A31
Packet Privacy and Net Neutrality
 Everybody’s familiar with consumer identity privacy, as in protecting passwords
and social security numbers and complying with HIPAA, GLBA, SOX, PIPEDA,
et al.
But what about packet privacy?
Everybody’s familiar with consumer identity privacy, as in protecting passwords
and social security numbers and complying with HIPAA, GLBA, SOX, PIPEDA,
et al.
But what about packet privacy?
Never mind net neutrality, I want my privacy. As in packet privacy. The telcos say they need to sell non-neutral routing of traffic to recover the cost of building broadband networks. Moving from the Internet, where a packet-is-a-packet, to something that looks suspiciously like the 20th century telephone network requires remarrying the content and connectivity that TCP/IP divorced. It requires deep packet inspection. It requires looking at the content of communication.Despite Berninger’s phrasing, packet privacy isn’t something separate from net neutrality: it’s one of the key features of it. The point is that net neutrality isn’t just about pricing policies or technical means of content routing: it’s about privacy. And privacy is an issue that everybody understands. Stifling, throttling, or disconnecting without announced limits, censoring, wiretapping, and espionage: these are all violations of packet privacy.AT&tT does not plan to roll out two physical pipes to every end point in order to sell Google enhanced access. The new telco plan calls for content-based routing to separate traffic into media and destination specific VPNs (Virtual Private Networks). Laws exist to address the substantial privacy threats created by the fact telephone companies know Mr. Smith called Mr. Jones, but the privacy risks associated with “content routing” replacing “end point routing” enter an different realm.
— Forget Neutrality — Keep Packets Private, by Daniel Berninger, GigaOm, Sunday, January 14, 2007 at 8:30 PM PT
-jsq
Moderate? Comcast Stifling Isn’t
 Promising unlimited access, not delivering, and refusing to admit it
is managing a network for the good of the many above the activities of the few?
Pete Abel thinks so:
Promising unlimited access, not delivering, and refusing to admit it
is managing a network for the good of the many above the activities of the few?
Pete Abel thinks so:
Earlier this month, Comcast — the nation’s largest cable broadband company — was caught doing what any good Internet Service Provider (ISP) should do, i.e., manage its network to ensure that the online activities of the few don’t interfere with the online activities of the many,The problem with Comcast stifling BitTorrent by faking reset packets from a participant is not that Comcast is trying to manage its network: it’s that Comcast used a technique that if it came from anyone other than an ISP would be considered malicious denial of service, that Comcast still hasn’t admitted doing it, and that Comcast bypassed numerous other methods of legitimate network management, such as those used by PlusNet. Comcast could even use the Australian model and sell access plans that state usage limits and throttle or charge or both for usage above those limits. What Comcast is doing it seems to me is much closer to the false advertising of unlimited access that got Verizon slapped down for wrongful account termination.Fair vs. Foul in Net Neutrality Debate, By Pete Abel, The Moderate Voice, 24 November 2007
The biggest problem with what Comcast (and Cox, and AT&T, and Verizon) are doing is that their typical customer has at most one or two choices, which in practice means that if your local cable company and your local telephone company choose to stifle, throttle, block, or terminate, you have no recourse, because there’s nowhere to go. Competition would fix that.
Abel tries to back up his peculiar interpretation of network management with revisionist history: Continue reading
PlusNet: Honest Prioritization
 Unlike
Comcast
and
Cox,
PlusNet
in the U.K. says what it is doing:
Unlike
Comcast
and
Cox,
PlusNet
in the U.K. says what it is doing:
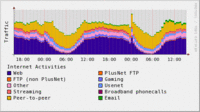
The principles of PlusNet’s network management policiesInterestingly, this list does not cite video as the most-favored application, instead it lists VoIP and gaming, which are participatory services. However, scan down to their table of types of traffic, and VoIP and gaming are Titanium, while video-on-demand is the highest level, Platinum. Continue reading— Traffic Prioritisation, PlusNet, accessed 26 Nov 2007
- To make sure that time-critical applications like VoIP and gaming are always prioritised
- To protect interactive applications like web-browsing and VPN from non-time sensitive download traffic
- To flex the network under demand to cope with normal peaks and troughs from day to day and month to month
- To flex the network more gracefully than other ISPs in the event of unusual demands in traffic or disaster situations such as a network failure
- To provide a service relative to the amount each customer pays in terms of usage and experience
- Provides a ‘quality of service’ effect, meaning multiple applications running on the same line interact with each other effectively, and use of high demand protocols like Peer-to-Peer doesn’t swamp time-sensitive traffic such as online gaming or a VoIP call.
Cox Interrupts eDonkey: Same Technique as Comcast with BitTorrent

The same person to bust Comcast’s blocking of BitTorrent traffic was called upon to test Cox’s system, and sure enough, he concluded with “conclusive proof” that eDonkey was getting the same treatment.First Comcast, Now Cox Busted ‘Managing’ Traffic by Jason Lee Miller, Webpronews.com, Mon, 11/19/2007 – 10:51.
We asked regular user Robb Topolski, who was the first to discover Comcast’s traffic shaping practices, to take a look at Cox connectivity a little more closely.The main difference between Comcast and Cox is that Cox says it’s doing it, for the good of the user, of course. Still, which users exactly asked for their ISP to fake TCP packets? And how long before Cox trips up some business users, Like Comcast stifling Lotus Notes?According to Topolski, Cox is in fact using traffic shaping to degrade p2p traffic. In analyzing a user log, he has concluded that Cox is using traffic shaping hardware to send forged TCP/IP packets with the RST (reset) flag set — with the goal of disrupting eDonkey traffic. He’s been unable to tell precisely what hardware Cox is using, but he notes that the technique being used is very similar to Comcast’s treatment of BitTorrent.
— Cox Also Disrupting P2P Traffic, Using the same forged packet method as Comcast, by Karl, BroadbandReports.com, 03:35PM Thursday Nov 15 2007
-jsq
Comcast Stifling BitTorrent
 This was expected (cablecos, like telcos, want “freedom to degrade”),
but is now confirmed:
This was expected (cablecos, like telcos, want “freedom to degrade”),
but is now confirmed:
Comcast Corp. actively interferes with attempts by some of its high-speed Internet subscribers to share files online, a move that runs counter to the tradition of treating all types of Net traffic equally.Comcast was denying blocking or throttling as recently as August (and as near as I can tell they still do deny it). Numerous users reported it, and the AP has now confirmed it. However, what Comcast is doing isn’t precisely throttling. Continue readingThe interference, which The Associated Press confirmed through nationwide tests, is the most drastic example yet of data discrimination by a U.S. Internet service provider. It involves company computers masquerading as those of its users.
If widely applied by other ISPs, the technology Comcast is using would be a crippling blow to the BitTorrent, eDonkey and Gnutella file-sharing networks. While these are mainly known as sources of copyright music, software and movies, BitTorrent in particular is emerging as a legitimate tool for quickly disseminating legal content.
— Comcast blocks some Internet traffic, Tests confirm data discrimination by number 2 U.S. service provider, by Jeff Chiu, AP, 19 Oct 2007
Freedom to Degrade
 BT made an interesting presentation at an IETF meeting
in which it described a spectrum whose endpoints are
BT made an interesting presentation at an IETF meeting
in which it described a spectrum whose endpoints are
My, freedom is so degrading. Continue reading
- demand side — freedom to degrade others
- …
- supply side — freedom to degrade competitors
— re-ECN architectural intent by Bob Briscoe, UCL, BT, 68th IETF, Unofficial Birds of a Feather (non-BoF), Prague, 21 Mar 2007
Incumbents Preparing
 Cringely gets pessimistic:
Cringely gets pessimistic:
In the end the ISPs are going to win this battle, you know. The only thing that will keep them from doing that is competition, something it is difficult to see coming along anytime soon, rather like that lemonade-powered sports car.Is he just whining? Continue reading— Beyond Net Neutrality: If at first you don’t succeed, change the game. I, Cringely, Pulpit, April 6, 2007
